Cracking Passwords with ColabCat

How secure is the password “pinkhouse79”. It’s 11 characters long which is not too bad. However, it only contains lowercase letters and numbers, and isn’t as complex as it could be. But does that matter? Does compelxity matter? Does length matter? Which matters MORE?
I used a tool called Colabcat that leverages Hashcat on Google Collaboration to attempt to crack 600 NTLM hashes of “simple” passwords generated by DinoPass, because I wanted to see how these passwords, which I consider to be above average for what non-security concious people use, would stand up.
Colabcat, combined with the rockyou wordlist and the OneRuletoRuleThemAll, was able to crack 256 of the 600 password hashes in just under 10 minutes - and the example password “pinkhouse79” was one of those cracked.
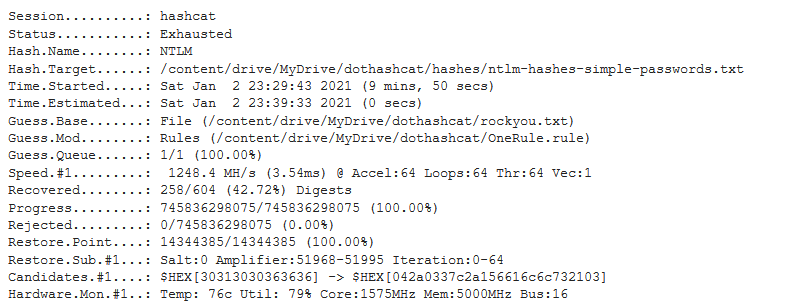
The reason 256 password hashes were cracked, and the others not, is because the rockyou wordlist contained, for example, the word “pink” and “house”. The other passwords generated by DinoPass had one or both their two combined words missing from the rockyou list and as a result were not able to be cracked. This could easily be overcome by changing up or customizing the wordlist to include more words.
However, rockyou and hashcat alone would not be enough to crack the password hash for “pinkhouse79”, but with OneRuletoRuleThemAll thrown into the mix hashcat is able to mix-and-match words in the list, and append characters at the beginning, end, and in between.
There are over 10,000 rules in OneRuletoRuleThemAll that emulate the patterns that most people use when creating passwords and drastically increases the likelihood of guessing their password. Rockyou contains 14,344,391 passwords. With OneRule that number increases to 745,836,298,075. And with Google graciously providing their Tesla T4 GPU for free, it is possible to generate those billions of hashes in less than 10 minutes.
What if the password was “PinkHouse79” or even “PinkHouse123!”. Surely, “PinkHouse123!” is uncrackable! It has uppercase, lowercase, numbers, special characters, and its 13 characters long! It has everything we’ve been told (read: forced) to include in our passwords for years because “security.” Well, both of these password hashes were also cracked in under 10 minutes on Colabcat using the same word and rules list, which are all free and publicly available to anyone.
In conclusion, with modern compute power and the intelligent way that adversaries are able to attack password hashes, the whole idea of a ‘password’ is completely dead. What is necessary today are “passphrases” that contain 4 or more words chosen at random and have no comprehensible meaning, with some special characters thrown into the mix (and not as placeholders for letters, i.e. ! subbing in for i). Duckduckgo will give you some ideas if you’re struggling, just search for “passphrase”.
Stay classy.
Robert